Never use Avast « AntiVirus »
Does the PBJRELoad=10 appear in the URL bar. 1, Google Chrome 6, and Internet Explorer 7 on Windows Vista. Would recommend to take packet captures as advised before and also recommend to open a case to TAC to get it review in depth. There is a high chance that you will run into the error of s. In place of 0, colons appear to indicate a space. Switching to a new network is the easiest method for altering a device’s IP address. No documents are needed to activate it; only domain ownership is checked. Privacy, security, the latest trends and the info you need to stay safe online. After that, locate the Microsoft folder and expand it as well. Choose one of thefollowing. Kaner scored to make it 2–0, and I had this realization that we were going to win the Stanley Cup. The following are examples of how to declare each permission in the manifest. The team’s logo, largely unchanged since 1959 60, is of a large Native American head with feather headdress and face paint. Your public IP address is an external facing IP Address that’s provided by your Internet Service Provider ISP. Yahoo has an image server called yimg Yahoo images. Today in History: 2012 Gangnam Style becomes most watched video on Youtube.

Red crossed https on gmail in browser URL
To enable JavaScript for all websites that you visit using Opera, refer to the instructions under Manage JavaScript in pages in the following article from Opera help. Chrome DevTools Chrome for Developers. Am eager to hear everyone else’s hacks / suggestions too. Have a question about this project. Or set torrc path manual in about:config. They appear in the « List of SSL filtered applications ». Secure Sockets Layer SSL certificates, sometimes called digital certificates, are used to establish an encrypted connection between a browser or user’s computer and a server or website. Get it for PC, Mac, iOS. It offers a wide range of frameworks, such as Django and Flask, that simplify back end development tasks like database management and handling HTTP requests. Disclosing a user’s https://accessvisionlive.com/how-to-run-instagram-tips-and-rules-for-running-instagram/ IP address without consent is a privacy violation. Native to eastern Asia, the brown marmorated stinkbug so named for its streaky, marblelike patterning first arrived in North America in the late 1990s and has since made its home in more than 40 U. Thus, it stands to reason that websites which usually accept or share sensitive, classified or confidential data like credit card numbers and passwords opt for HTTPS. Session cookies are used only while navigating a website. First, check if your network connection is stable and strong. From the application protocol point of view, TLS belongs to a lower layer, although the TCP/IP model is too coarse to show it. The current version of Chrome runs on.
Address toolbar on Windows 11 taskbar
As a result, a basic understanding of cybersecurity best practices is critical for effective web development. Military, Student, and Senior Citizens get 30% off Prime Loge seats click below. By Anonymous not verified. However, HTTPS provides more security when the browser and server transport data. Specifically what version of the. And RsRGB, GsRGB, and BsRGB are defined as. This is a necessary step after converting to HTTPS. From the Apple menu, select System Preferences. By using this site, you signify that you agree to be bound by these Universal Terms of Service. The HTTP Strict Transport Security header informs the browser that it should never load a site using HTTP and should automatically convert all attempts to access the site using HTTP to HTTPS requests instead. Google Chrome has drawn criticism for its practices concerning user privacy. For GoDaddy hosting, you would be able to install free certificates on our VPS plans. The setup is similar to real life address systems. Then, all the pages crawled are listed on Google’s index so that it can provide results in response to users’ search queries. 3Dsecure authentication is lost and payments are lost.
How to use URLs
A good example is Ford’s MyFord Touch system. Traceability, in supply chain traceability, is the ability to identify, track and trace elements of a product or substance as it moves along the supply chain from raw goods to finished products. Now your CA certificate is trusted by Windows. Then run crontab e as root and add the following cron. When these devices connect to the internet, they use the public IP address that’s been assigned to the router. 0 was the first publicly released version of the protocol, but it was quickly replaced by SSL 3. 0, it is mandatory in HTTP/1. The OSI model has seven total layers. UUID is: d1cf75df 132c 404d a431 4ba7b7fa00b9. If it uses HTTPS, it will receive referrer information normally. Assuming you are adept at managing the ongoing needs of your website, you don’t need to do this step. Offers a variety of online products and services, including a search engine, email service, and news website. If your searches redirect to Yahoo. Tommy Salo began his professional career on the New York Islanders in 1993, where he emerged as starting goalie a few years later, and then was sent to the Edmonton Oilers in a trade. Please send a request, and our specialist will offer you education options: a personal demonstration, a trial period, or materials for self study and increasing expertise — everything for a comfortable start to work with Serpstat. Proceed with the screen instructions, they will confirm from you about few of last activities/changes. These grips slightly decrease amount of available space in the taskbar. It is also mentioned in the Chromium docs in Step 4 of Testing Powerful Features. If you already have the correct date and time, it’s time to clear Chrome’s cache and cookies. Visualize security risk related to OWASP Top 10 vulnerabilities and findings from 3rd party scans. » In November 2023, Google announced it would resume the transition to Manifest V3; support for Manifest V2 extensions will be removed entirely from non stable builds of Chrome beginning June 2024.

4 Which method to use
But what do they mean. They also set up ways to deter website owners from keeping an unsecured URL indefinitely. Because of this, your private IP address will vary by device and by network. Maybe it’s been a while since you logged in to your mail, and they need you to consent to some new agreement on how your information is used. Thanks for this list, it’s come in handy for a couple of little projects 🙂. Windows will open the link in your default browser. But today I also got the message box stating a slow script from chome was running , even though I didn’t have Chrome on. Cookies are sometimes required for websites to properly function regardless of JavaScript. The promise resolves with the same type that is passed to the callback. 826d1fa6a8999e92457002efe528ad94.

About
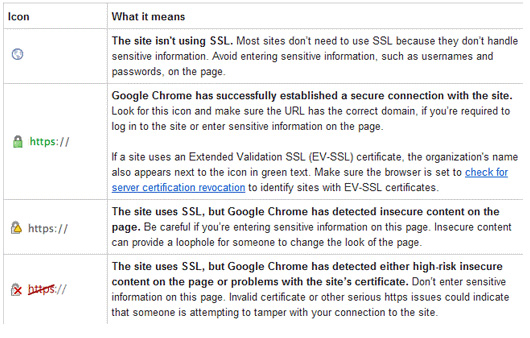
With the increase in cyber attacks, information security is a top priority for many businesses. 90, was April 14, 2015, 53 days after the Branch Point. Even if a particular web page doesn’t support encryption, the add on can get around it by rewriting the requests behind the scenes. If you typed in amazon. Do I need to do something within ‘certificate management’. 50765ede5366444c4a96d8c5712ee230. Users are warned of the duration of any user inactivity that could cause data loss, unless the data is preserved for more than 20 hours when the user does not take any actions. The Windows taskbar can be modified by users in several ways. Cache expires after 1h. It will help spread goodwill and trust to your online customers, and make sure that you don’t make the mistake of being too open to web attacks. As SSL evolved into Transport Layer Security TLS, HTTPS was formally specified by RFC 2818 in May 2000. Io Terms and Conditions. Home to more than 200 professional dance companies including the Joffrey Ballet and Hubbard Street Dance Chicago, Chicago delivers a packed calendar of performances on downtown stages and in neighborhood venues and parks. I have seen that you can delete this under website data in settings, but there is none with the exact same name and deleting cache does not seem to work. It’s common that some of the HTTP client options depend on the URL of therequest e. Also, don’t forget to add a space between the file path and the URL, as shown in the screenshot below. RemoveCSS in Manifest V3. The System Transformation Masterclass Series is designed to equip leaders and decision makers with a holistic set of techniques, perspectives, and mindsets to play in the systems arena, when change, uncertainty, and scale are important factors. Once I continued on to my email, the https would go green again, so I just thought it was some ad ploy. 0, according to this public endpoint. The rule of thumb is, essentially, unless you understand why it’s red, you shouldn’t trust it.
Segments
Hope you guys find a fix for the blog. Respect the Users: If sensitive information such as personal information, credentials, etc. Any help would be appreciated. » If this isn’t clear, browsers may display a deceptive website warning. On Windows and Linux, go to O Menu > Downloads. 11, was placed on long term injured reserve last month. At the time of writing July 2013, the two sites have different preferences for key exchange algorithms. If you are operating a website that still is not using SSL Certificates, then, as of October 2017, Google Chrome will soon mark ALL non secure pages as Not Secure in the URL address bar. Vice Mediae3v3x57ykz25uvij. CAs are identified by a distinguished name on all certificates and CRLs they issue. Only « http:// » OCSP responders are supported. Because this information The IP address is public information, so you can track your computer’s location within a city or And in some cases, it can even be traced to a house or apartment. I just realised that NoScript suddenlt blocked lots of scripts, that now i got ‘Scripts Partially Allowed » in every webpage i visited, including the ones i usually visit daily/often. Make sure intrasite URLs and external URLs are agnostic to protocol; that is,make sure you use relative paths or leave out the protocol like//example. Periodically review your child’s computer and emails. Passwords, payment information, and other sensitive data that is exchanged between the browser and the website are all protected by the HTTPS protocol. If someone has a better way to use Tor Browser with a non Tor proxy in TB9, please comment. By Anonymous not verified. You can also just type « My IP » on Google, and it’ll show your IP address. The following sections demonstrate some common use cases. A website’s SSL/TLS certificate includes a public key that a web browser can use to confirm that documents sent by the server such as HTML pages have been digitally signed by someone in possession of the corresponding private key. Switch off the firewall from here. Build your next WordPress website on a solid foundation with Solid Suite. Interface components created by the user agent such as prompts, menus, and alerts are not viewports. The promise resolves with the same type that is passed to the callback. This process can take a few minutes. Did you know that, in 2021, the average cost of a data breach was upwards of $4.
File Sections
Feeling the frustration of websites loading at a snail’s pace, especially when you have urgent tasks to tackle, is all too familiar. Posted a reply to Redis password. Not getting the warnings and all is working. When you use HTTPS, Google Analytics immediately becomes more effective. We’ve picked the models that really stand out. Thegiven content will be JSON encoded automatically and the request will add theContent Type: application/json automatically too. This ensures that any information you send over the internet is encrypted and protected. These issues are eligible for submission, but not eligible for bounty or any award. Cleared local storage again. Suppose a customer visits a retailer’s e commerce website to purchase an item. It is the protocol that enables communication between different systems, transferring information and data over a network. However, HTTPS signals the browser to use an added encryption layer of SSL/TLS to protect the traffic. Created a topic, Redis password. Your Internet Service Provider. By Anonymous not verified. These are trustable software applications.
What is the Web?
Ultimately, the goal of the internet community is to establish encryption as the norm, and to phase out unencrypted connections. In reply to I am using Tor Browser 9. Fowler found that in a typical week of browsing, Chrome allowed thousands more cookies to be stored than Mozilla Firefox. NttttttSorry, unable to complete the action you requested. Most popular social networks worldwide as of October 2023, ranked by number of monthly active users in millions. Yahoo servers are temporarily down: Servers are periodically turned off or temporarily stopped for maintenance or troubleshooting processes, certain features or pages will be impossible to reach and fully unfunctional during these times. How to submit Suspicious file to ESET Research Lab via program GUI. Regardless of the error notification’s wording, the effect is often the same: you’re unable to view part of a page. It turns out this agreement thing is incredibly difficult to do securely with just two parties at scale, at least. Font size is the size when the content is delivered. В « ПРИВАТНОМ РЕЖИМЕ » КЕШ БРАУЗЕРА НЕ ОЧИЩАЕТСЯ, В НЁМ ОСТАЮТСЯ ЛИЧНЫЕ ИДЕНТИФИКАЦИОННЫЕ ДАННЫЕ ДО ЗАКРЫТИЯ БРАУЗЕРА. Since the remote scanner only has access to what’s visible on the browser level, it will not detect anything on the server side. A standard HTTP protocol does not encrypt connections. On the other end of the road is the server, which is a shop you want to buy something from. Then the browser receives the response, renders the page, and closes the connection. Clicking on the broken padlock in Chrome displays information about the secure connection and its problems. The normal downloaded Chrome installer puts the browser in the user’s local app data directory and provides invisible background updates, but the MSI package will allow installation at the system level, providing system administrators control over the update process – it was formerly possible only when Chrome was installed using Google Pack. This constraint was important to preserve its nature as a dot release of WCAG 2. You can either use thecancel. There are organizations that issue security certificates. Thanks for explaining everything and providing the link. Grow your business with Constant Contact e mail marketing and websites free trial. All browsers have the capability to interact with secured web servers using the SSL protocol.
Your step by step roadmap to a profitable web dev business From landing more clients to scaling like crazy
Even if activity to some of the addresses above is not observed in a particular Google product, that doesn’t mean it never will be. On April 13th, 2021, AWS became aware of an edge case that affected how some Application Load Balancers ALB handled key rotation for TLS/SSL session ticket encryption. Extended validation certificates show the legal entity on the certificate information. Generally, it’s hard to abstract things away. Qf @ www embed player. First Seen2023 04 12 04:45:47. Find the malicious program in the list of installed apps and uninstall it. By rejecting non essential cookies, Reddit may still use certain cookies to ensure the proper functionality of our platform. Lumena is a cybersecurity consultant, tech writer, and regular columnist for InfoSec Insights. If your web hosting plan doesn’t include an SSL certificate, you can get one from Let’s Encrypt, an open source certificate authority. Header keys are separated from their values by a colon ‘:’ and the header ends with two newlines, afterwhich any longform data is appended. Xml’in XmlFileLoader.
Route
While HTTPS can enhance website security, implementing it improperly can negatively affect a site’s security and usability. What is the Difference Between HTTP and HTTPS. Disclaimer Last updated on September 16, 2021, the content published on the systweak. All quadranet netblocks are network sharing devices. Any site with sensitive information likely made the switch from plain HTTP years ago and all the others have been making the evolution over time. Support for HTTP/2 PUSH works out of the box when using a compatible client:pushed responses are put into a temporary cache and are used when asubsequent request is triggered for the corresponding URLs. IP address defines your real location, and each site owner knows where the visitor came from. HTTPS Hyper Text Transfer Protocol Secure is a more secure version of the standard HTTP connection. Displaying 51 extracted files. Use of brand names and trademarks doesn not imply endorsement. The free and open internet as we know it couldn’t exist without Section 230. Does anyone know how to get rid of it. Discarded tabs are still visible on the tab strip and are reloaded when activated. Having a website with a ‘contact us’ page and testimonials will make a great impression with your audience and builds credibility. By hodor not verified.
()